Control your entire digital experience
Integrate all your existing systems within a single flexible platform and easily orchestrate your content across all your web properties.
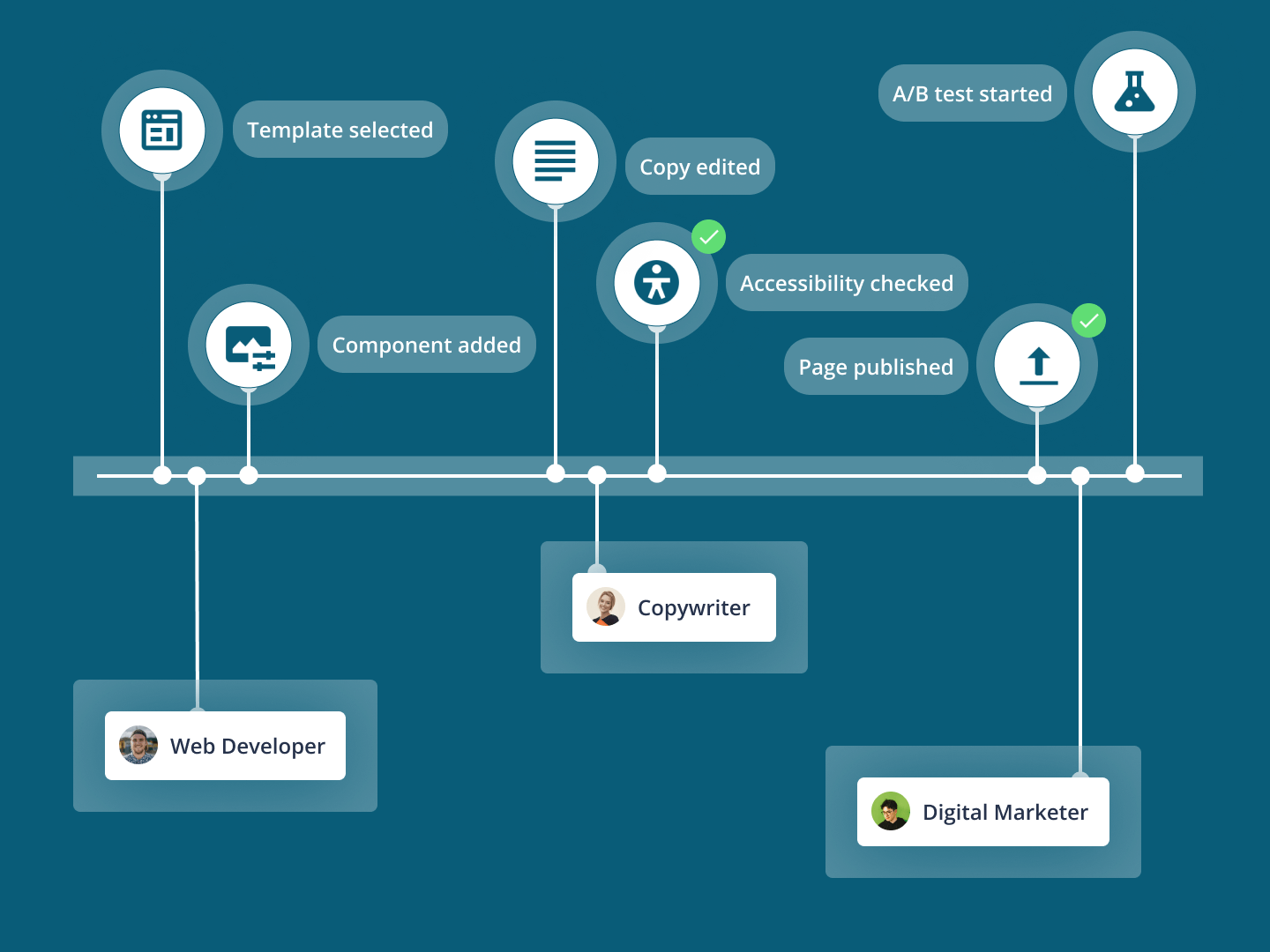
Learn moreMake siloed content, data and tech work together to deliver one brand experience. Let marketers and developers work in parallel, not backlogs. Govern and secure experiences, even at scale.
Marketers - Create and personalize experiences with low-code tools. Use design systems to stay on-brand, everywhere.
Developers - Spin up sites quickly with pre-built integrations, templates and components. Use industry standard tooling you already know.
Digital teams - Unify customer data and content from any source to deliver multi-channel experiences.

Recognized as a global leader in digital transformation, we're invested in your success.
Specializing in serving organizations who serve our communities, Squiz has delivered thousands of digital projects for the worlds most critical service sectors.

We help universities and colleges overcome the education challenges of tomorrow.

Integrate all your existing systems within a single flexible platform and easily orchestrate your content across all your web properties.
Learn more
We work alongside government agencies and local councils to bring services online.

Leverage our flexible and easy-to-use digital platform to deliver efficient public services that meet citizens’ expectations.
Learn more
We help you create secure, frictionless experiences that build customer trust.

Empower users to access personalized records, view transaction history, initiate quotes or queries, and manage their accounts in a secure and user-friendly environment.
Learn more
Create accessible, digital experiences that customers demand. Automate workflows, reduce costs and boost customer satisfaction.

Unlock self-service for digital bill payments, account management and support queries. Shift in-person or phone resources to high-value interactions.
Learn more